Can you pinpoint the weakest link in your organisation’s cyber security infrastructure?
According to the FBI, CEO fraud is now a $12 billion scam [1]. Yet some of us remain completely unaware of this style of attack.
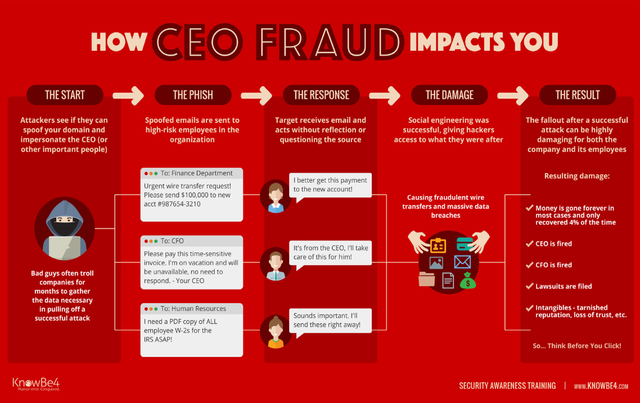
So what is CEO fraud? Well this scam, often also referred to as a BEC (business email compromise) [2] involves the impersonation of a senior company executive to target key employees (such as those with roles in accounting or HR). It attempts to defraud them into transacting unauthorised monetary transfers or confidential tax information [3][4].
As niche as the style of attack may be, it has a 90% success rate [5]. In 2018, Lloyds Bank estimated that an eye-watering half a million companies in the UK had already been hit by CEO fraud [6]. Some of the biggest victims are well-known brands that you would expect to have their cyber security procedures perfected:
• Save the Children sent $1m to an attacker after receiving fake invoices from an employee’s email [7]
• Google and Facebook transferred a total of $123m to an attacker after he posed as an IT security reseller [8]
• Mattel temporarily lost $3m to attackers before contacting the FBI and the bank the money was transferred to in China and retrieving the money [9]
• Ubiquiti Networks after an attacker impersonated an employee and an executive the business transferred $46.7 million to various bank accounts held by the attackers [9].
In reality anyone in any company can be the weakest link.
Lloyds’ survey indicated that 53% of respondents said the attackers had posed as their bosses [6]. With such a successful hit rate you may be wondering how such attacks are carried out? Well CEO fraud attacks can be executed in one of four ways:
1) Phishing: Emails posing as renowned and trustworthy brands (often including legitimate logos) are sent to hundreds of users in tandem, in an attempt to deceive them into forfeiting sensitive information [4]. A particular concern is that phishing has now surpassed ransomware as the most common attack vector [10].
2) Spear Phishing: When an attacker has gathered intelligence on the user, they can create more personalised emails and target them using information which is more likely to grab the user’s attention [4].
3) Whaling: This is an attack aimed at high-level individuals within a business (such as executives or administrators) and will typically use personalisation and intelligence such as names or known companies the business may transact with in order to fraudulently acquire money or confidential data [4].
4) Social Engineering: This type of attack relies on human interaction and uses your social surroundings such as someone you are familiar with like a friend, family member or in some cases a celebrity. This often includes an email or “DM” on social media containing a link or download which embeds malware on the user’s device [3].
Understanding how CEO fraud may be carried out is part of combating these attacks. All end users, including high authority users, can be your weakest link and without correctly training and educating your end users, you are missing an essential first line defence against cyber crime.
Are you aware of how vulnerable your business could be to an attack? If not how can you find out and how can you better protect your business?
(1) End User Training and Education
CEO fraud targets your last and most vulnerable line of defence . Preventative action includes training and educating end users. This facilitates the ability to spot a phish attempt (e.g. a slight difference in email address or spelling mistakes in the body of the email). Above all training ensures better communication processes, encouraging employees check with the “sender” before processing payments or responding to anything within a malicious email.
(2) Phishing Simulations
Using real world phishing templates, you can deploy simulated attacks and track users reactions. You will have the tools to evaluate and train users on attachments, embedded links, personal data requests and spoofed emails. Educating your users through simulated attacks provides first-hand knowledge and is designed to change behaviour when faced with a phishing attack by improving awareness and allowing you to implement your own “how to” preventative guides.
(3) DMARC – Domain-based Message Authentication Reporting and Conformance
DMARC – an email authentication technology – ensures emails passing through your networks are trustworthy, blocking spoofing domains. To pass authentication, the domain name must match the hidden “from” address and DKIM signature domain. If an email fails authentication DMARC will quarantine (move to spam), or reject (block delivery to your mailbox). Providing an essential first line of defence against CEO fraud and BEC attacks as end users will not always be reliable with fraudulent email detection. DMARC is a robust but complex security protocol and can often be hard to deploy and configure correctly. There are commercial solutions available to assist and strengthen DMRAC deployment such as Sentinel from Barracuda Network’s or OnDMARC by Red Sift.
Don’t look for a technology fix to a human problem! Instead make your end users an effective last line of defence to ensure your business has a better chance of standing up to a cyber-attack. To learn more, please get in touch.
Sources:
[1] https://www.ic3.gov/media/2018/180712.aspx
[2] https://www.trendmicro.com/vinfo/us/security/definition/business-email-compromise-(bec)
[3] https://businessadvice.co.uk/tax-and-admin/invoicing/what-is-ceo-fraud-and-how-can-i-identify-it/
[4] https://www.knowbe4.com/ceo-fraud
[5] https://www.infosecurity-magazine.com/news/isc2congressemea-ceo-fraud/
[6] https://www.computerweekly.com/news/252448102/Half-a-million-UK-firms-hit-by-CEO-fraud-Lloyds-Bank-estimates
[7] https://www.infosecurity-magazine.com/news/save-the-children-hit-by-1m-bec/
[8] https://www.secureworldexpo.com/industry-news/google-facebook-bec-business-email-compromise
[9] https://resources.infosecinstitute.com/5-real-world-examples-business-email-compromise
[10] https://www.infosecurity-magazine.com/news/phishing-surpasses-ransomware/