I previously wrote about the 3-2-1 principle and the "reduction" in protection many organisations have following a move to a cloud-centric or cloud-hybrid environment: 3-2-1 (the Autodata 101!)
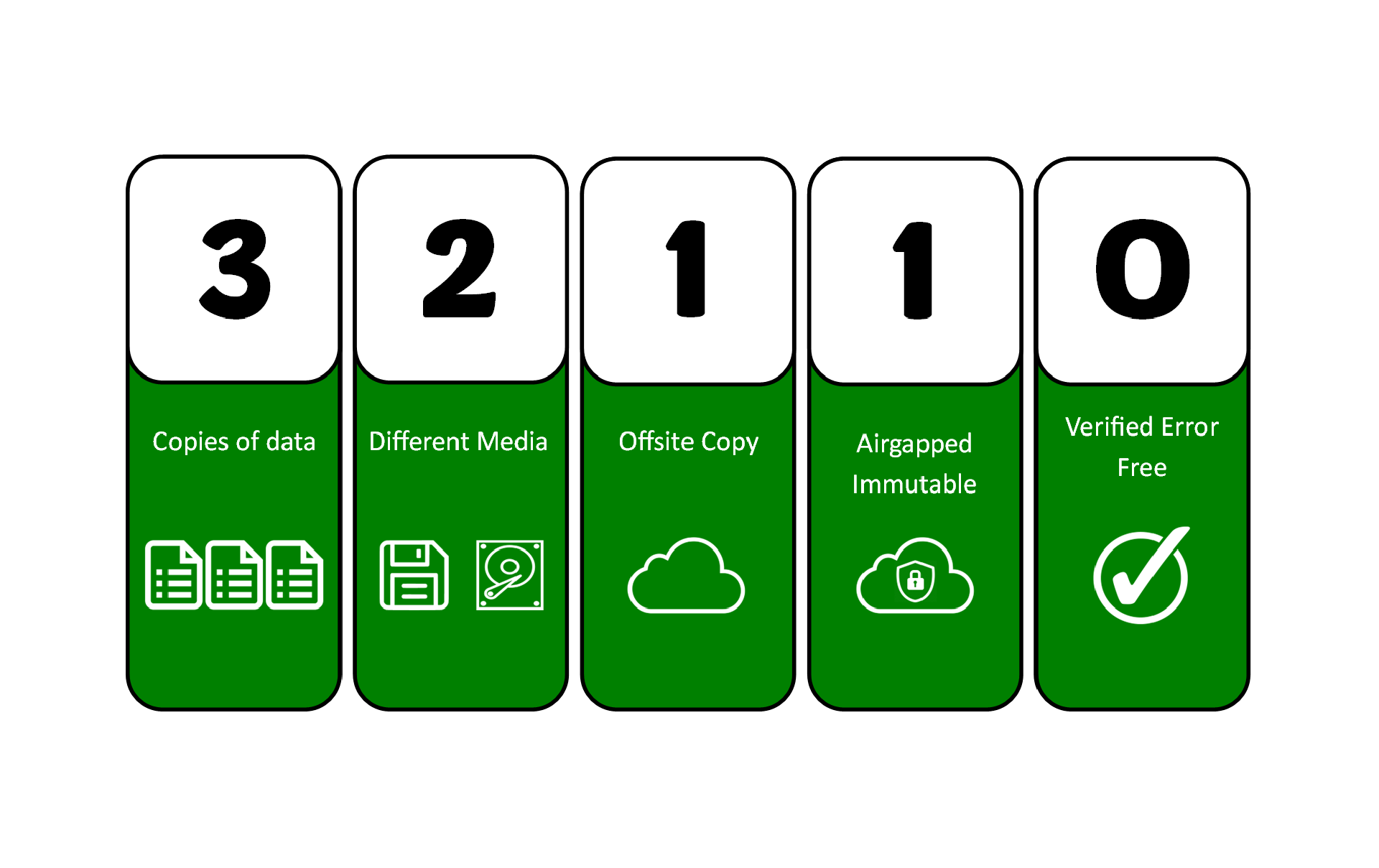
However 3-2-1-1-0 is fast becoming the new standard, whether that's for compliance, insurance purposes, or just simply to help protect against more severe attacks such as ransomware.
So what is it?
As before it relates to:
- backing up 3 copies of your data
- stored on 2 different media types
- of which 1 is offsite
With the addition of:
- 1 copy being airgapped and immutable
- all with 0 verified errors
Let's take a look at the benefits these additions grant:
3-2-1-1-0 ... Adding Airgapping and Immutability
If YOU have access to edit and modify your backups, so does a cyber criminal! You therefore need to ensure that the transition from your on-premise backup to your offsite backup is completely separate ... separate systems, different logins, secondary MFA ... which should provide a basic level of protection and forms the airgapped element of the policy.
Immutability is the second and most important element. True immutability should ensure the data cannot be altered, deleted, moved or in any other way affected for a pre-determined period of time neither by YOU nor your PROVIDER nor ultimately any would-be attacker.
Many modern backup solutions and storage providers (both on premise and cloud) support immutability but many are not “TRUE” i.e. you can override the policy, if there is a backdoor for you there’s a backdoor to be exploited, therefore we always recommend you confirm the level of lock your storage or service provider can deliver, not all immutability is created equally!
How will this affect your solution?
If your offsite copy supports immutability, is outside of your primary environment (preferably within a different storage provider) and meets your RTO and RPO needs, then maybe not at all. It could just be a straightforward case of configuring correctly to meet your data-protection needs.
What this element gives you is the knowledge that in the event of accidental data loss, inside threats, or external threats, you can always recover. With backups being a primary target for attack, “just having a backup” is no longer enough, as without any immutability it is very likely that backup will also be compromised!
3-2-1-1-0 ... Ensuring Verified Backups with Zero Errors
It may seem obvious, but a backup is only as good as the data it captures and protects, yet testing of backups on a regular, planned schedule is missing from many backup routines which is easily done when dealing with the numerous tasks of the day. Modern backup solutions will “test” backups have been taken correctly (if configured accordingly) but good practice and data-health is a must.
If there are errors, why?
Again modern backup tools will typically come with or can be added to to deliver detailed reports explaining exactly where the errors lie and often how to resolve them. If you have a larger estate with multiple backup repositories look into tools that will give you a single pane of glass across the estate so backup jobs can be viewed centrally, if it’s easy to monitor it’s much more likely issues will be resolved quickly and data protected.
Additionally you should be performing regular restore tests (and preferably have this automatically monitored). It’s all well and good that when a solution is implemented you are sure of meeting your RPO/RTO objectives but 6-12-18 months in, data has increased, system availability reduced can you be sure these requirements can still be met? Only with a combination of manual and automatic testing.